STAY UPDATED

Checking File Integrity With FCIV
In this blog post, we dicuss the use of Microsoft File Integrity Checksum Verifier (FCIV) and the importance it has in security. FCIV is a command line utility that is
Android GPS Spoofing
There are many reasons you may want fake the location of your Android via GPS spoofing. Whatever the reason may be, this blog post will explain how to do so

Open Board View Installation
Open Board Viewer or OBV for short is a program that is used for viewing .brd or board schematic repairs. This software is widely used by board repair mechanics and

Kali Linux Live USB Creation
Creating a live USB version of Kali Linux has many perks. Live USBs provide the additional benefit of enhanced privacy because users can easily carry the USB device with them or

Apache Tomcat – WAR Backdoor
Apache Tomcat versions 7-9 contain a vulnerability within the WAR deployment setting which allows a malicious user to upload and deploy a JSP backdoor. In this blog post, we will

Zenmap System Security Evaluation
Nmap & Zenmap Zenmap is the official GUI version of nmap, a multi-platform network security scanner. (Windows, Linux, Mac OS X, etc). It is free and open source, easy for

Rogue AP – Your WiFi Belongs to Us
So i just got home from a long day of work & per usual, my phone automajically connects to my WPA2 home wireless network. Upon unlocking my phone, a prompt

Penetration Test Directory – Sharpen Your IT Skills
Our penetration test directory contains intentionally vulnerable machines, websites to hack, and boxes to pop for weeks on end…legally of course… Metasploitable Metasploitable 2 Metasploitable 3 Metasploitable is virtual machine

VPN Filter Catapults Its Way Through Devices
Cisco Talos Intelligence VPN Filter Findings & IOC Update Recent discoveries regarding the VPNFilter malware have been made by Cisco Talos and various other intelligence partners. It has beend etermined
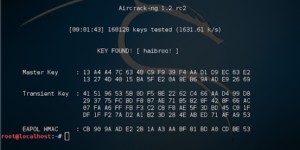
WPA2 Hacking & Cracking – Aircrack
(Please use this as an informative post. This method is obsolete as there are tools mentioned at the bottom of the post to automate this process. Following this step by
Phishing Types & Techniques
In the early days, phishing had begun with mass emailing to reel in potential victims. This attack type generally produced fair results considering it only took a couple victims to
KRACK – Breaking WPA2 Security
A recent weakness has been discovered in the WPA2 Wi-Fi protocol. Attackers are using a method called KRACK (Key Reinstallation Attack) to exploit the weakness on a wide range of

EternalBlue: Exploiting & Patching
The recent WannaCry & Petya ransomware utilize the EternalBlue exploit to own machines and load malware. EternalBlue is a remote code exploit targeted at a vulnerability in SMBv1 and NBT
Benefits of Content Filtering
Content filtering helps to filter acceptable content for viewing and accessing. The system administrator decides upon which content is acceptable or unacceptable for viewing and or accessing. When content filtering
